Election fraud case documents accuse over 20 Chinese companies of cyberattack. Data outlines method of attack, network details, specific manipulation allegations and more in evidence package
How did a pillow salesman obtain a robust package of cybersecurity data? That’s the first question we have when looking…
How did a pillow salesman obtain a robust package of cybersecurity data? That’s the first question we have when looking at this document and others filed in Lindell v. US Dominion, Inc in a district court in Minneapolis.
To clarify, this reporting neither supports or denies any validity of the content provided. We are only confirming that these documents do in fact exist and encourage our readers to do their own research.
The case, filed originally on June 3rd, 2021, contains one specific piece of evidence from Mike Lindell that we didn’t expect to see. The report filed alleges a cyberattack from Chinese, Ukrainian and South Korean networks providing incredibly explicit details about those networks, companies and methods of entry into county voting machines across the United States.
Support the national challenger by donating cryptocurrency with the button below.
We think it’s worth noting that the data provided is not vague in any capacity, and honestly I think it’s worth understanding where this data was gained. We’ll highlight some examples below.
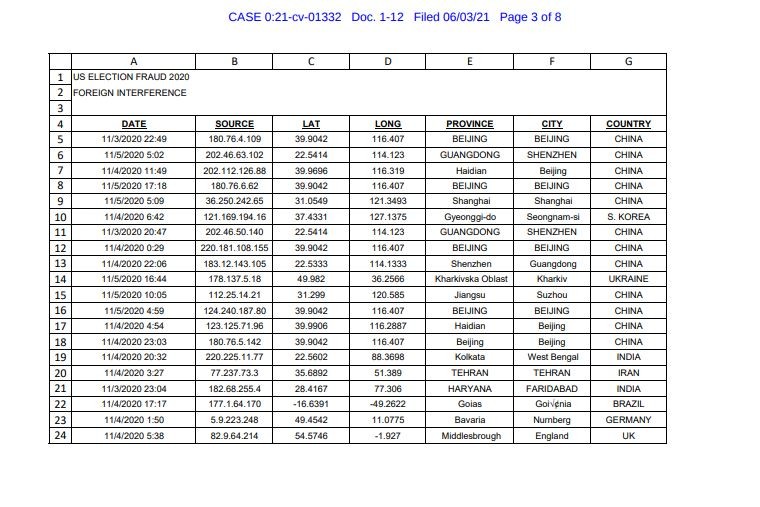
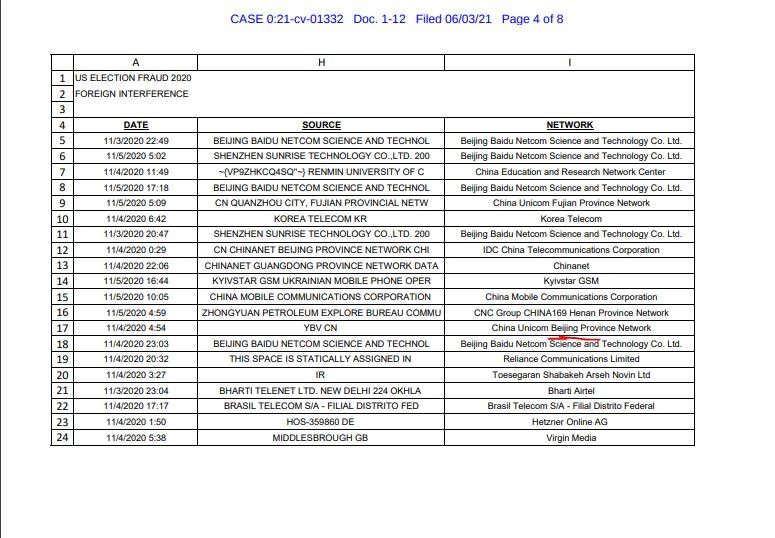
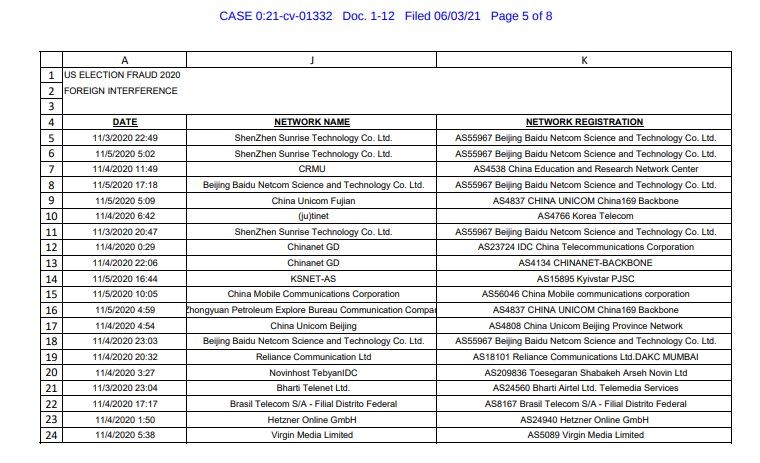
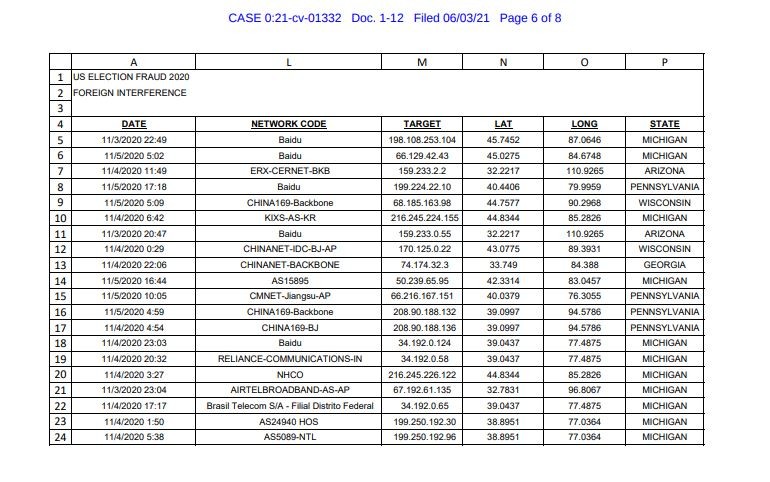
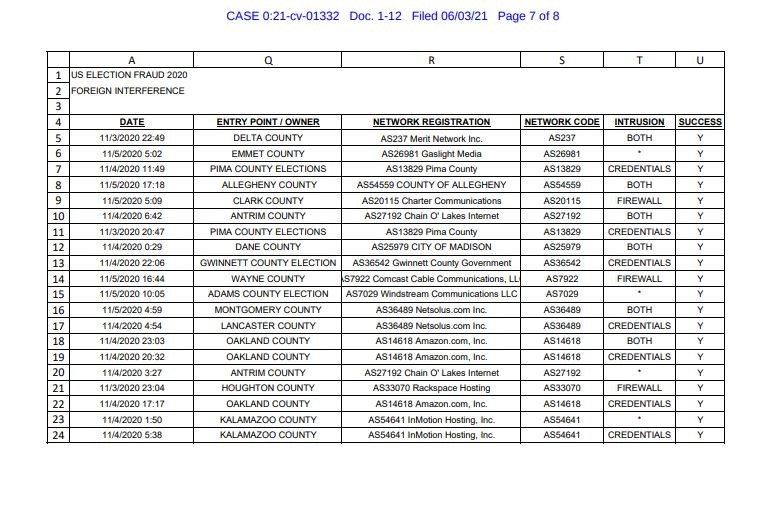
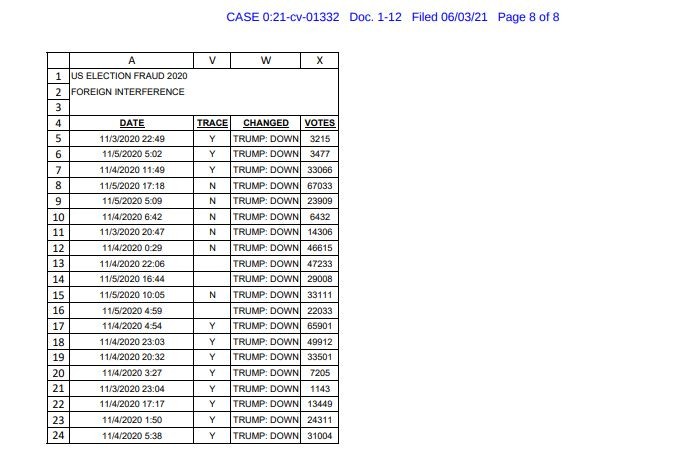
Regardless of the validity of these accusations, it’s hard to deny that the data presented lacks detail, as it covers nearly every single aspect imaginable and appears to be state of the art in terms of the data collected on what the documents and allege.
Overall, it’s been 8 months since the 2020 election day and there is still a flurry of legal action taking place surrounding it, the sooner we discuss and highlight the validity or lack of validity to these claims, the sooner America can heal.